The internet has become an essential part of our lives, and we use it every day to access a wide range of information and services. As we interact with different websites, we come across various acronyms, and one of the most common ones is HTTPS.
When browsing the internet, you may have noticed that some websites start with HTTP, while others start with HTTPS. HTTP stands for Hypertext Transfer Protocol, while HTTPS stands for Hypertext Transfer Protocol Secure [1]. The addition of the letter “S” signifies that the connection between your browser and the website is secure, but what does it mean?
In today’s digital age, cybersecurity has become a significant concern, and the use of HTTPS has become increasingly important. HTTPS is a protocol that uses encryption to protect data transmitted between a website and a user’s device. When you enter sensitive information such as credit card details or passwords on a website, HTTPS ensures that the data is transmitted securely and cannot be intercepted by unauthorized third parties.
The “S” in HTTPS is an indication that the website has an SSL/TLS certificate, which enables the encryption of data between the website and the user’s device [2]. SSL (Secure Sockets Layer) and its successor, TLS (Transport Layer Security), are cryptographic protocols that provide secure communication over the Internet. When you access a website with HTTPS, your browser initiates a “handshake” with the website’s server, and both parties agree on a set of encryption protocols to use for data transmission.
In this article, we will explore the importance of HTTPS in ensuring secure communication over the Internet and how SSL/TLS certificates work to provide this security. We will also discuss the potential risks of not using HTTPS and the importance of ensuring that websites use HTTPS to protect sensitive information.
Hypertext Transfer Protocol Secure (HTTPS) Overview:
The internet has become a staple part of our daily lives. With the increase in online activities such as online shopping, banking, and social media, security on the internet is becoming a primary concern. HTTPS or Hypertext Transfer Protocol Secure is a protocol that is designed to protect the security and privacy of internet users. HTTPS is a secure version of HTTP, the primary protocol used for transferring data over the internet.
Usage in Websites
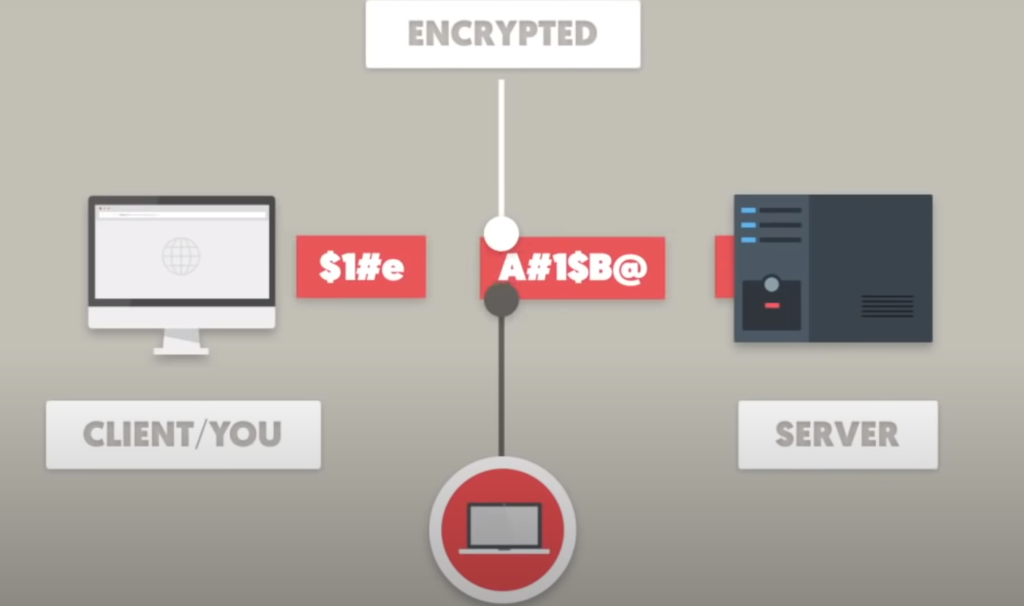
In addition to providing security for sensitive information, HTTPS is also important for website owners as it can help to build trust with their users. The use of HTTPS on a website is indicated by a padlock icon in the browser’s address bar, which signals to users that the website is secure and that their data is protected.
Browser Integration
HTTPS is supported by all major web browsers including Google Chrome, Firefox, Safari, and Microsoft Edge. Web browsers display a padlock icon in the address bar to indicate that the website is using HTTPS. The padlock icon is accompanied by the word “Secure” or “Not Secure” to indicate whether the website is using HTTPS or not [3].
In addition to indicating whether a website is secure, web browsers also display warning messages to users when they try to access websites that are not secure. For example, Google Chrome displays a warning message that says “Not Secure” in the address bar when users try to access websites that are not using HTTPS.
Security
HTTPS provides security by encrypting the data that is transmitted between a user’s computer and the website’s server. Encryption is the process of converting data into a code that can only be deciphered by authorized parties. The use of encryption ensures that the data transmitted over the internet is protected from unauthorized access and interception.
HTTPS also uses a digital certificate to authenticate the website’s identity. Digital certificates are issued by trusted third-party organizations called certificate authorities (CAs). The digital certificate contains information about the website’s identity and public key. When a user connects to a website using HTTPS, the website’s server sends its digital certificate to the user’s browser.
The browser then verifies the authenticity of the digital certificate by checking that it was issued by a trusted CA and that it has not been revoked. If the digital certificate is valid, the browser uses the public key contained in the certificate to establish a secure connection with the website’s server.
Technical
When a website is secured with HTTPS, the communication between your browser and the website server is encrypted. This encryption process occurs with the help of an SSL (Secure Sockets Layer) or TLS (Transport Layer Security). Both of these cryptographic protocols authenticate data transfers between two or more systems to ensure secure transmission.
The “S” in HTTPS stands for Secure [4]. The acronym essentially means that all communications sent over HTTP are encrypted using SSL/TLS protocol. This makes any data exchange more secure than it would be without security measures like HTTPS. All major websites utilize this technology to keep user data safe from malicious actors, allowing users to confidently browse the web without worrying about their personal information being exposed.
In addition to providing a layer of encryption for data transfers, HTTPS also provides authentication. This means that users can be sure that the website they are accessing is actually the one that it claims to be. To authenticate a website as legitimate and secure, the server must present a valid SSL/TLS certificate. This certificate contains important information about the website, like its owner and its public key (used for encryption). By verifying this information before allowing access, HTTPS ensures that users don’t accidentally end up on malicious websites or fall prey to phishing attacks.
How Does HTTPS Work?
HTTPS (Hypertext Transfer Protocol Secure) is a protocol used to secure communication between a web server and a client, typically a web browser. It is an extension of the standard HTTP protocol but uses an encryption mechanism to protect the confidentiality and integrity of data transmitted between the server and client.
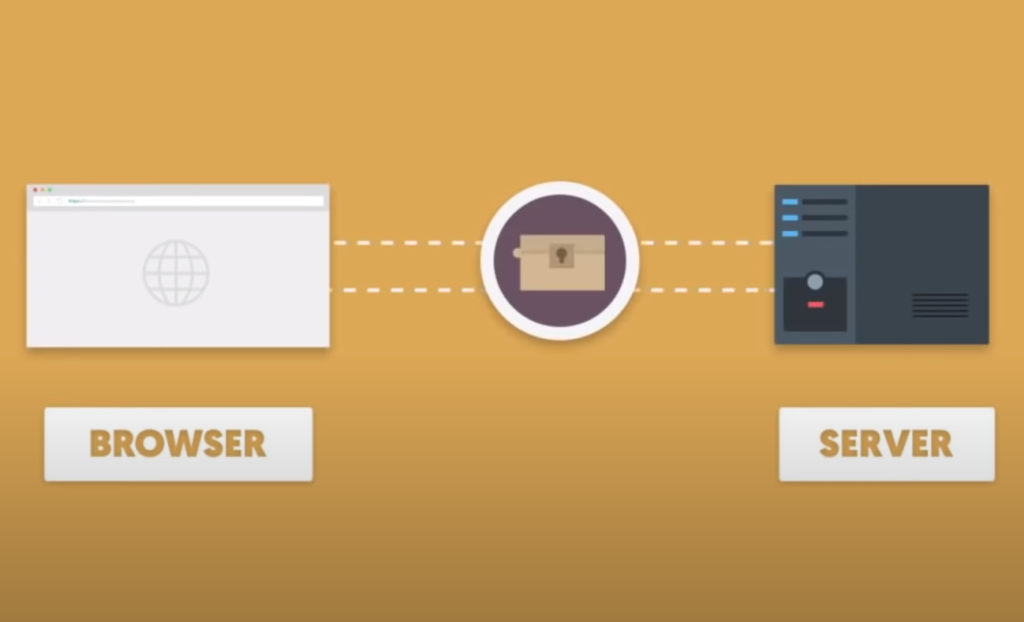
Here is a simplified overview of how HTTPS works:
- The client initiates a connection: When a user types a website URL starting with “https://” into their browser, the browser initiates a request to connect to the server hosting the website;
- The server responds with its SSL certificate: The server responds by sending its SSL (Secure Sockets Layer) certificate to the client’s browser. This certificate contains information such as the website’s domain name, the public key for the website’s encryption, and the certificate authority (CA) that issued the certificate;
- The browser verifies the SSL certificate: The browser verifies the SSL certificate by checking that it was issued by a trusted CA and that it is still valid. If the certificate is valid, the browser sends a message to the server acknowledging that it trusts the certificate;
- Browser and server negotiate encryption: The browser and server then negotiate a shared encryption key to be used for the remainder of the session. This process is known as the SSL handshake;
- Encrypted communication: Once the encryption key is established, the client and server can exchange encrypted data, such as login credentials or credit card information, without the risk of interception or tampering by a third party [5];
Difference Between HTTPS From HTTP:
1) Network Layers Involved
HTTPS stands for Hypertext Transfer Protocol over Secure Socket Layer (SSL). It is also known as HTTP over TLS or Transport Layer Security.
The main difference between HTTPS and HTTP is that HTTPS uses an encryption layer to secure the transmitted data while HTTP does not. The security layer in HTTPS makes use of key exchange, authentication, encryption, and message integrity technologies to ensure communication privacy.
When an HTTPS connection is established between two computers, the data travels through several layers of encryption:
- The secure socket layer (SSL) encrypts the information at the transport layer;
- The cipher suite and digital signature algorithms provide authentication and message integrity services;
- Additional encryption protocols may be used to further protect sensitive data;
At the end of its journey, when the information reaches its destination, it is decrypted by both layers before being delivered securely. Thus HTTPS ensures that all communication between a user’s computer and a server is confidential and protected from unauthorized access or tampering [6].
2) Server Setup
HTTPS stands for HyperText Transfer Protocol Secure. It is a secure version of the HTTP protocol, which is used to send and receive data over the Internet. HTTPS works by encrypting the communication between servers and clients (browsers), preventing third parties from intercepting the transmitted information. For an HTTPS connection to be established, both the client and server must have certain settings in place.
On the server side, several components need to be set up correctly: web server software such as Apache or IIS, an SSL/TLS certificate, and port 443 open on any firewall that may be installed. The SSL/TLS certificate is necessary because it provides encryption of the data being transmitted between the server and the client. It also serves as a trust mechanism, allowing visitors to know that their data is secure. Port 443 needs to be open so that HTTPS requests can reach the web server.
Once all of these components are set up correctly, the server should be able to properly serve content over HTTPS. Visitors should see “HTTPS” in the address bar of their browser if they have successfully connected to an HTTPS website.
3) Acquiring Certificates
The key component of setting up a secure HTTPS connection is the SSL/TLS certificate. These certificates are issued by an entity known as a Certificate Authority (CA). To obtain one, you will need to have a valid domain name and access to the website’s server. You will also need to provide information about your organization such as contact details and company address.
Once all of this information has been gathered, you can submit it to a CA for processing. After they verify that the information is correct, they will issue an SSL/TLS certificate which you can then install on the server. This process usually takes between 1-2 business days.
4) Use As Access Control
HTTPS can also be used as an effective access control mechanism. For example, if a user attempts to access a secure website without the required credentials, their request will not be granted and they won’t be able to view the content. This prevents unauthorized individuals from accessing sensitive data that is stored on the server.
HTTPS is a powerful tool for keeping online data secure and preventing malicious attacks from being successful. By setting up an HTTPS connection correctly and acquiring an SSL/TLS certificate, web developers can ensure that visitors have peace of mind when visiting their websites [7].
5) In Case Of Compromised Secret (Private) Key
If a malicious actor can gain access to the secret key, then they can decrypt data that was encrypted with it. This means that any communication sent over HTTPS is vulnerable to being intercepted and viewed by attackers.
To mitigate this risk, HTTPS also uses public key encryption. A website’s public key is known and can be used to encrypt data before it is transmitted over the internet. The web server then uses its private key to decrypt the data upon receipt. This ensures that even if an attacker were to gain access to the website’s secret key, their ability to read sensitive information would still be limited as they wouldn’t have access to the corresponding public key needed for decryption.
6) Certificate Revocation
Another important element of HTTPS security is Certificate Revocation. This means that if a website’s digital certificate becomes invalid, either due to tampering or expiration, web browsers can quickly detect and alert the user by checking with a central list of revoked certificates. This ensures that users who connect to a site via HTTPS are not defrauded by a malicious website that is falsely claiming to be authentic. Certificate revocation is an essential component of HTTPS security and helps keep users safe from fraudulent websites.
Without it, there would be no way to know if the website being visited was legitimate or not. When using an HTTPS connection, Certificate Revocation is automatically checked every time a user visits a site, providing peace of mind that the website they are visiting is secure.
HTTPS provides an added layer of security when browsing the web, ensuring users can access sites securely without having to worry about their data falling into the wrong hands. The “S” in HTTPS stands for “secure” and its Certificate Revocation feature ensures users remain safe online.
Limitations of HTTPS
Despite its many advantages, HTTPS is not a perfect security solution. Although it encrypts data in transit, once the communication reaches its destination (e.g., the web server), that data may still be vulnerable to attack or misuse. For example, if a website stores passwords or other sensitive information on its servers, those credentials can still be stolen by attackers who have gained access to those systems [8].
In addition, HTTPS does not protect against spoofing attacks where an attacker pretends to be a legitimate website to gain access to user credentials. This type of attack relies on manipulating domain name resolution, which is outside the scope of HTTPS protections. Users need to remain vigilant and aware of these types of attacks and take appropriate security measures to protect their data.
HTTPS and the CIA Triad
On the other hand, the CIA Triad is a framework used to guide information security policies and practices. CIA stands for Confidentiality, Integrity, and Availability [9]. These three principles form the foundation of information security and aim to protect data from unauthorized access, modification, or destruction. Confidentiality ensures that data is accessible only to authorized users or processes,
Integrity ensures that data is accurate and trustworthy, and Availability ensures that data is accessible to authorized users when needed.
When it comes to HTTPS, it directly addresses the principle of Confidentiality by encrypting the data in transit. It ensures that only authorized parties can access the data, and prevents eavesdropping and interception by unauthorized parties. However, HTTPS does not directly address the principles of Integrity and Availability, which are also important in the context of cybersecurity.
Advantages of HTTPS:
- Enhanced security: Requesting and transmitting data over HTTP can be vulnerable to malicious attacks such as man-in-the-middle attacks, where someone can snoop in on the communications between your computer and a website. With HTTPS, encrypted data is passed through secure connections which makes it difficult for third parties to intercept it;
- Trustworthiness of websites: For those who are concerned about privacy, visiting an HTTPS-secured website offers more assurance that a site is legitimate than one without encryption. Sites with HTTPS have been verified (using digital certificates) to ensure they haven’t been tampered with or spoofed;
- Increases search engine rankings: Search engines favor sites using HTTPS, providing them a slight ranking boost in comparison to those using HTTP. A secure website also makes it easier for visitors to trust your site, resulting in more traffic;
- Data integrity: HTTPS helps protect websites from data corruption during transmission and storage by making sure that the data is transferred correctly between clients and servers. This helps ensure that only intended individuals can access sensitive information, like credit card numbers or passwords [10];
Common Mistakes To Avoid When Adapting HTTPS Connection
Adapting HTTPS (Hypertext Transfer Protocol Secure) connection is an essential step in enhancing the security and privacy of your website. However, there are common mistakes that you should avoid when making the switch. These include:
- Failing to Redirect HTTP to HTTPS: After adapting HTTPS, it’s essential to redirect HTTP traffic to HTTPS. This ensures that all traffic to your website is encrypted, and users are not exposed to security risks. Failing to do so can result in duplicate content, security risks, and negative SEO impacts;
- Not Validating SSL/TLS Certificate: SSL/TLS certificate validation is essential for ensuring that the certificate was issued by a trusted authority and that the website’s identity is authentic. Failing to validate the certificate can lead to security risks such as man-in-the-middle attacks and phishing scams;
- Ignoring Mixed Content Warnings: Mixed content warnings occur when a website loads both secure and insecure content simultaneously. This can result in security risks and warnings for users. It’s essential to fix all mixed content warnings by ensuring that all website components (images, scripts, and stylesheets) are loaded over HTTPS;
- Forgetting to Update Canonical Tags: Canonical tags tell search engines which version of the website content to index. Failing to update canonical tags can result in the indexing of duplicate content, negative SEO impacts, and security risks;
- Overlooking HSTS Implementation: HSTS (HTTP Strict Transport Security) is an essential security measure that ensures that all communication between the server and the browser is encrypted over HTTPS. Failing to implement HSTS can expose your website to security risks such as SSL stripping attacks;
- Not Monitoring HTTPS Status: HTTPS is not a one-time implementation, but a continuous process. It’s essential to monitor your website’s HTTPS status regularly and ensure that all website components are correctly loaded over HTTPS [11];
Are HTTPS Connections Vulnerable To Attacks?
While HTTPS (Hypertext Transfer Protocol Secure) connections provide a significant level of security and encryption, they are not entirely immune to attacks.
Here are some examples of attacks that can still occur on HTTPS connections:
- Man-in-the-middle (MITM) attacks: MITM attacks occur when a third party intercepts communication between the server and the client, allowing them to view and modify data in transit. HTTPS connections are vulnerable to MITM attacks if the attacker can bypass the SSL/TLS certificate verification process;
- SSL/TLS vulnerabilities: SSL/TLS vulnerabilities can be exploited by attackers to compromise the security of HTTPS connections. For example, the Heartbleed vulnerability discovered in 2014 allowed attackers to access sensitive data from servers that used vulnerable versions of OpenSSL;
- Malware: Malware can infect client or server systems and intercept data transmitted over HTTPS connections, compromising their security. Malware can also exploit vulnerabilities in SSL/TLS implementations to gain access to sensitive data;
- Social engineering: Social engineering attacks can trick users into revealing sensitive information, such as login credentials or personal information, to attackers. HTTPS connections cannot protect against social engineering attacks, as they rely on user behavior rather than technical vulnerabilities;
- DNS spoofing: DNS spoofing involves redirecting traffic to a fake website by manipulating the DNS resolution process. HTTPS connections are vulnerable to DNS spoofing attacks if the attacker can redirect traffic to a fake website with a valid SSL/TLS certificate [12];
Things to Be Aware of Before Switching to HTTPS
Switching to HTTPS (Hypertext Transfer Protocol Secure) is an important step in improving the security and privacy of your website.
However, you should be aware before making the switch of several things:
- Obtain an SSL/TLS Certificate: To switch to HTTPS, you will need to obtain an SSL/TLS certificate. This certificate will authenticate your website and enable encryption of the data exchanged between the server and the browser. You can obtain a certificate from a trusted certificate authority (CA) or use a free certificate provided by Let’s Encrypt;
- Check Compatibility: Before making the switch, you should check the compatibility of your website and all its components (including plugins, scripts, and other third-party services) with HTTPS. Some components may not work properly over HTTPS or may cause compatibility issues that can affect the functionality of your website;
- Update Internal Links: After switching to HTTPS, you will need to update all internal links on your website to point to the new secure URLs. This includes links within your website’s content, as well as links within scripts and stylesheets;
- Check External Links: You should also check external links that point to your website and ensure that they are updated to point to the new HTTPS URLs. This will prevent any “mixed content” warnings that can affect the security of your website;
- Consider Performance: HTTPS encryption can have a slight impact on the performance of your website, particularly on older devices or slower connections. You should consider implementing performance optimization techniques such as HTTP/2 and content delivery networks (CDNs) to mitigate any impact on site speed;
- Update Google Analytics: If you use Google Analytics, you will need to update your website profile to use HTTPS URLs. This will ensure that your website data is accurately tracked and reported;
- Monitor for Errors: After making the switch, it is important to monitor your website for any errors or issues that may arise. You should regularly check your website’s HTTPS status and ensure that all components are functioning correctly;

FAQ:
- What does “S” signify in HTTPS?
The “S” in HTTPS stands for “Secure”. HTTPS is an acronym for “Hyper Text Transfer Protocol Secure”. It is a secure version of HTTP that uses encryption to protect data sent between a web server and a web browser [13].
- Is the “S” in HTTPS important?
Yes, the “S” in HTTPS is very important. It indicates that the connection between your web browser and the website you are visiting is secure and that any data exchanged between the two is encrypted and protected from interception by third parties.
- What does removing “S” from HTTPS do?
Removing the “S” from HTTPS changes the connection from a secure encrypted connection to an unsecured one. This means that any data transmitted between the website and the user can be intercepted and read by third parties.
- What does the first “S” stand for in SSL?
The first “S” in SSL stands for “Secure”. SSL stands for Secure Sockets Layer, which is a protocol used for establishing secure connections over the internet.
- How is SSL different from HTTPS?
SSL is a security protocol used to establish secure connections between a web server and a web browser. HTTPS is a secure version of the HTTP protocol that uses SSL/TLS encryption to protect data sent between the server and the browser.
- How do I remove “S” from HTTPS in Chrome?
You cannot remove the “S” from HTTPS in Chrome. The “S” indicates that the connection is secure and encrypted. If you try to remove it, you will be redirected to an unsecured connection or receive a warning message that the connection is not secure.
- How do I know if a link is safe?
You can check if a link is safe by looking for the “https: //” prefix in the URL, which indicates that the connection is secure and encrypted [14]. You can also look for a lock icon in the address bar, which indicates that the website has a valid SSL/TLS certificate. Additionally, you can use a website reputation service, such as Google Safe Browsing, to check if a website is known to be malicious or unsafe.
- How do I open an unsecured website?
You can open an unsecured website by simply entering the website address in the browser’s address bar. However, you should be aware that unsecured websites do not use encryption to protect data transmitted between the website and your browser, which can make your data vulnerable to interception by third parties.
- Does HTTPS use SSL or TLS?
HTTPS can use either SSL or TLS encryption protocols to secure the connection between the web server and the web browser. SSL has largely been replaced by TLS, which is a more secure and up-to-date encryption protocol.
- Can an HTTPS site be hacked?
While HTTPS is a secure protocol, it is not 100% foolproof and HTTPS sites can still be hacked. However, HTTPS does provide a significant level of protection against common attacks, such as man-in-the-middle attacks and data interception.
- Why is HTTPS safer?
HTTPS is safer than HTTP because it encrypts the data sent between a web server and a web browser, making it more difficult for third parties to intercept and read the data. HTTPS also ensures that the website you are visiting is legitimate and has a valid SSL/TLS certificate, which helps protect against phishing attacks.
- Can you decrypt HTTPS?
It is possible to decrypt HTTPS traffic, but it requires sophisticated hacking techniques and is generally not feasible for most attackers. HTTPS encryption is designed to protect data from interception and decryption.
- Is Google HTTPS encrypted?
Yes, Google uses HTTPS encryption to protect data transmitted between its web servers and users’ web browsers. This helps to protect against data interception and provides a higher level of security for users.
- Is HTTPS encrypted over WiFi?
Yes, HTTPS encryption works over WiFi connections just like it does over wired connections. The encryption is applied to the data sent between the web server and the web browser, regardless of the type of network connection used.
- Why are Chinese websites not using HTTPS?
Chinese websites are not necessarily any less likely to use HTTPS than websites in other countries. However, some Chinese websites may not use HTTPS encryption due to a lack of awareness or resources, or because the website owners do not consider it a priority.
- Does HTTPS hide your IP?
No, HTTPS encryption does not hide your IP address. Your IP address is still visible to the web server you are connecting to, even if the connection is encrypted.
- Can HTTPS give viruses?
No, HTTPS encryption does not give viruses. HTTPS is a security protocol used to protect data transmitted between a web server and a web browser, and it does not have any inherent ability to deliver viruses or malware.
- Do websites use TLS or SSL?
While SSL was widely used in the past, most websites today use the more secure TLS encryption protocol. TLS is the successor to SSL and is designed to provide stronger encryption and better protection against attacks. However, some websites may still use SSL if they have not updated their security protocols.
Useful Video: How HTTPS Works?
References:
- https://www.computerworld.com/article/3021276/why-the-s-in-https-is-important.html
- https://www.healthit.gov/faq/what-does-https-web-address-mean
- https://www.quora.com/What-does-the-S-stand-for-in-HTTPS
- https://smallbusiness.chron.com/client-server-programming-42314.html
- https://en.wikipedia.org/wiki/HTTPS
- https://www.f5.com/company/blog/the-s-in-https-doesnt-stand-for-ssl
- https://www.watchtowerhq.co/what-does-the-s-in-https-stand-for/
- https://cwatch.comodo.com/blog/website-security/what-is-https-and-why-switching-to-https/
- https://www.wiredtitan.com/what-does-the-s-in-https-stand-for/
- https://www.cloudflare.com/learning/ssl/what-is-https/
- https://www.techtarget.com/searchsoftwarequality/definition/HTTPS
- https://www.lifewire.com/what-do-http-and-https-stand-for-3482375
- https://www.websecurity.digicert.com/security-topics/what-is-ssl-tls-https
- https://www.globalsign.com/en/blog/the-difference-between-http-and-https








Leave a Reply