Do you know what electricity is? In school, we learned the definition: “This is a flow of charged particles.” Enough to satisfy curiosity and turn the light on and off without wondering what actually makes the light bulb glow. If someone wants to understand the nature of electricity deeper, then the first thing he surprisingly finds out is that scientists still know almost nothing about electricity, and the school definition doesn’t really explain anything. But this never prevented me, you, Albert Einstein, or Robert Oppenheimer from pressing the switch and getting the result.
So it is with the Internet. We know that different protocols and algorithms are used to transfer data. At the same time, most often we do not even ponder what all these HTTP, IP and the like are mean in plain English. And everything is OK with it. We just enjoy, surfing sites, downloading files, sending e-mail. Connecting to various services that ensure our security, for example, directing our traffic through secure VPN tunnels, we do not have to rack our brains at all, thinking how exactly our protection is organized and why using a VPN is considered a reliable guarantee of our anonymity and the inaccessibility of our data for prying eyes.
However, if you nevertheless decide to figure out how everything works and why everyone who, wandering the vastness of the World Wide Web, wants to keep their privacy and not allow anyone to look at their files, except for those to whom they are directly intended, uses a VPN, then I have good news for you. Unlike electricity, not only scientists but also the author of this article knows enough about protocols and algorithms to explain it in simple terms.
So, first of all, let’s clarify what some abbreviations mean
- VPN – Virtual Private Network.
- IP – Internet Protocol.
- IPSec – three words: Internet Protocol and Security that are put together.
Very briefly. Internet Protocol – this is the basic protocol that allows other internet algorithms to identify a certain user (or to be more exact, the device he uses to enter the internet) and to “represent” him in the destination point like a well-schooled butler. This yesterday’s advantage nowadays appears a big problem. Although various “Corporations of Goodness” are eager to know everything about each of our steps and to sell this knowledge to zillions of firms whose main purpose is to make us consume whatever they are ready to sell. Of course, we do not discount the numerous state and private intelligence agencies that are passionately interested in our data for far less innocent purposes than the relatively harmless advertisers and sellers.
This is why hiding your IP has become as natural a security measure today as using a mask in public. As the saying goes: “if you are not paranoid, it does not mean that you are not being spied”.
Right in order to protect your real identity from all these greedy eyes for other people’s secrets exists VPN solution. IPSec – is the set of protocols in the architecture of most VPN applications that are responsible for the secure transfer of each bit of your data and providing your anonymity.
In particular, IPSec encrypts your data at the very beginning of your internet trip and decrypts at the point of final destination.
At the dawn of their existence VPN services used IPv4 protocol for providing security of data sent through the tunnels of a Virtual Private Network. But the time goes on, technologies get more and more complex and reliable. IPv4 grew up to IPv6. In 1994 Internet Architecture Board published the report “Internet Architecture Security”. As a practical conclusion of this research, the new standards of protected protocols were established. IPSec became one of them. Actually, we may say that IPSec is the enhancement of the well-proven security algorithm IPv4.
To explain how it works it’s necessary to realize what OSI (Open Systems Interconnection) model means.
OSI can be called a universal language used to transmit and receive any information on the Internet.
This language is based on the idea of seven conditional layers, into which any information is divided, regardless of format, extension or volume, transmitted via Internet channels.
There are these layers:
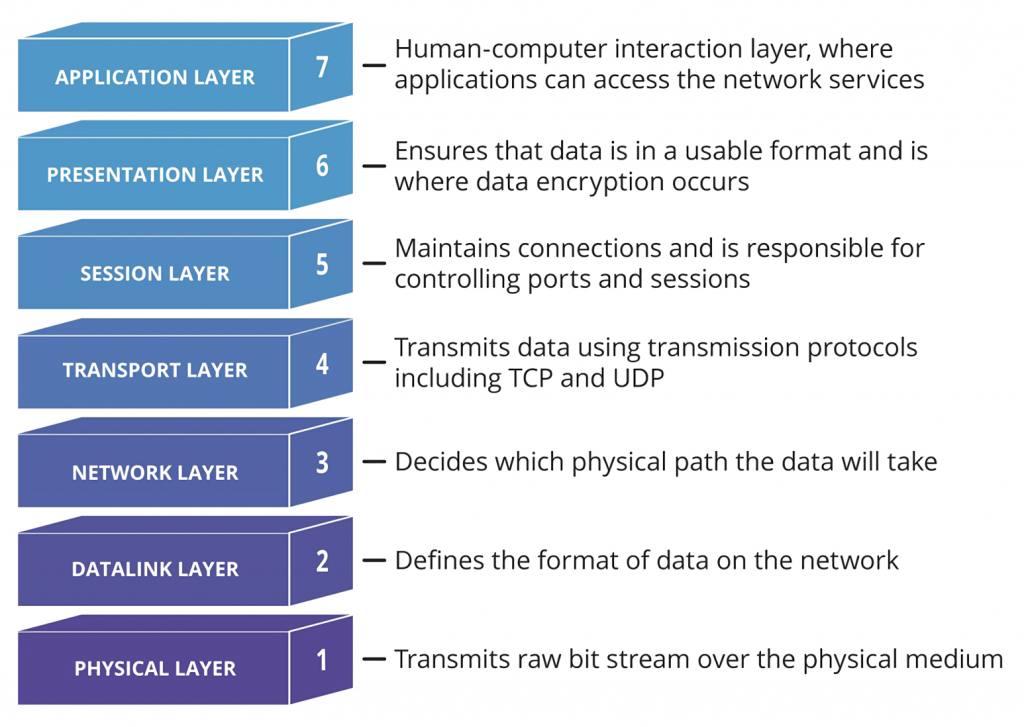
Different hacking techniques (such as DDoS attacks, application-layer attacks, protocol-layer attacks), as it is clear from their names, target the exact layers of OSI. And each secure protocol (in a narrow sense) is responsible for the protection of a certain level of this model. That’s why an efficient security solution implies not a single protocol but a set of them, as it is realized in IPSec.
Some other widespread security protocols are also actively used by different VPN applications. Particularly TSL (Transport Layer Security) and SSH (Secure Shell). TSL as it is obvious from the name guards level 4 – the Transport one. SSH covers the Application level (number 7). Unlike them, IPSec protects the middle – Network level (number 3).
What does the difference in these approaches mean?
The choice of the protection policy for different algorithms used in VPN applications is always a sort of compromise. Choosing levels 2 and 3, developers get freedom from a type of transportation. But this, in turn, means the need for fine-tuning and configuration of each application. The concentration of guarding measures on levels 5-7 means that usage of these solutions is virtually universal for different applications but providing this type of protection is strictly dependent on the exact type of transport protocol, for instance, PPP of Ethernet.
On these conditions, IPSec, based upon the middle – third – level, turns out flexible enough for protection of all IP-based protocols: User Datagram Protocol (UDP) and Transmission Control Protocol (TCP). On another hand, this approach allows an immense number of applications to easily operate with this set of algorithms.
As IPSec uses end-to-end encryption, hackers may get access to the user’s data if a password will be guessed or stolen. To avoid such leaks, the IPSec architecture includes two-factor authentication. If all security measures are taken, even the hijacking of a passphrase won’t open the gates of your cyber citadel for data hunters.
To describe the main principle that IPSec uses to protect user’s data it’s enough to say that the whole massive of information sent through the VPN connection gets broken into small pieces called packets. Each of these packets has a set of individual IDs that allow the program to put them together at the endpoint, but at the same time leave them completely unreadable for any outer observer, even if he manages to intercept some of these packets. After all, each of these fragments is also encrypted.
After the packets are assembled into a single whole, IPSec checks its seals, with which the fragments were marked before sending, with its own final identifier to make sure that the information has not been tampered with or altered by intruders during transmission.
As it was stressed in the very beginning, IPSec is a collection of several secure protocols. Let’s just list them.
- Authentication Header (AH)
- Encapsulating Security Protocol (ESP)
- Security Association (SA)
The functionality of each of them is clear because of their names.
- AH checks the headers of each packet at the exit and the assemblage point to be sure that nothing was lost or missed.
- ESP encrypts the headers of the packets before they are sent and decrypts when the transmission is over.
- SA is responsible for ensuring that keys and encryption algorithms recognize each other.
Usually, IPSec operates through port 500 on a computer.









Leave a Reply