Although it is possible for VPNs to be hacked, it would take an extraordinary amount of time and effort to do so. Leading VPN providers use OpenVPN or WireGuard protocols combined with AES or ChaCha encryption – a practically unbreakable code. Even though a VPN can’t make you unhackable, it does greatly lower the chance of being hacked.
There are many talks these days about VPNs and the security they provide. People are asking whether a VPN can be hacked. The answer to that question is yes, a VPN can be hacked. However, that does not mean you should avoid using them altogether. In this blog post, we will discuss the various ways in which a VPN can be hacked and what you can do to protect yourself. We will also provide some tips for choosing a secure and reliable VPN service.
What Is VPN Encryption and How Does It Work?
A VPN is a great way to improve your online security, but only if it’s properly encrypted. We decided to find out how secure popular VPN services really are. In the end, it comes down to encryption and whether or not your chosen VPN leaks any information.
This makes it difficult for anybody, including your Internet Service Provider, from seeing what websites you visit.By using a VPN, your messages will stay private and intact as they go through the public Internet.
VPNs transmit and encrypt your private data using a specific protocol. Protocols are an agreed-upon set of rules for data transmission and encryption. Most VPN providers give users the option to choose from several VPN protocols, including Point-to-Point Tunneling Protocol (PPTP), Layer Two Tunneling Protocol (L2TP), Internet Protocol Security (IPSec), and OpenVPN (SSL/TLS) [1].
The OpenVPN protocol is open-source, meaning that anyone can find and patch vulnerabilities. It’s considered one of the best options for VPN security by many people in the tech industry. If you’ve used a premium VPN service like ExpressVPN, then it’s likely that you’ve used OpenVPN without even knowing it!
A VPN protects your data by encrypting it so that it can’t be read by anyone other than the intended recipient. This is done using a cipher, which is an algorithm that dictates how the encryption and decryption process takes place within the VPN protocols.
The benefits and drawbacks of each VPN protocol depend on the cryptographic algorithm it uses. Many cipher options let users choose from different algorithms, which belong to one of three categories: symmetric, asymmetric, or hashing.
Symmetric encryption employs a single key to lock and unlock data, while asymmetric encryption takes advantage of two keys – one for encrypting information and another for decrypting it.
The solution to the inherent barriers in symmetric cryptography is asymmetric cryptography. Whitfield Diffie and Martin Hellman were part of the initial group that worked to resolve these issues by creating an asymmetric algorithm called Diffie-Hellman [2].
Diffie-Hellman is a well-known encryption algorithm among cryptographers on which many VPN protocols, such as HTTPS, SSH, and OpenVPN are based upon. This allows two individuals who have never met before to negotiate a secret key over an insecure public channel, like the Internet.
Hashing is a one-way, irreversible type of encryption that is used to protect data. An example of this would be storing passwords in an unreadable format. To check if the messages being sent are real, most VPN protocols use hashing algorithms. Some examples include MD5, SHA-1, and SHA-2; however, both MD5 and SHA-1 are now insecure methods.
Even though VPNs are highly effective in keeping data private, it is crucial to remember that no method is infallible. This becomes more pertinent if you’ve deemed a high-value target by possible enemies with the time and resources needed to go through with an attack. The “silver lining” is that most people don’t fall into this camp and are unlikely to be specifically targeted.
There are two ways to break into a VPN connection: breaking the encryption or stealing the key. Individuals who engage in activities such as hacking and cryptoanalysis use cryptographic attacks to decipher encrypted text without the key. However, this process is very resource-intensive and can often take years to successfully break the encryption.
Unlike taking the time to decrypt data, most cyber criminals find stealing encryption keys much easier. For example, this is generally the method of choice for spy agencies because the math behind encryption can be taxing to compute. Therefore, it’s more convenient to steal a key and save time and energy. Cheating, court orders, and VPNs make it easier for them to succeed. Although a VPN can be hacked, it’s much more complicated to do so than if you aren’t using one.
The research team recommends that service providers use 2048-bit or more Diffie-Hellman keys. They have also published a guide to deploying it for TLS. Furthermore, the latest revisions of protocols require longer prime numbers and the Internet Engineering Task Force (IETF) agrees with this sentiment.
Common VPN Weaknesses (Software & Hardware)
Lack of Encryption Standards
When it comes to VPNs, not all encryption is created equal. Some VPNs may only offer outdated or weak encryption standards, leaving your data vulnerable to attack.
Weak Passwords
Another vulnerability that can leave your VPN open to hacking is using weak or easily guessable passwords for your account and/or device. It’s crucial to use unique, complex passwords and enable multi-factor authentication when available.
Network Leaks
The way that most VPN users’ data gets compromised is not from an external party hacking the server. In reality, it’s mostly because of weaknesses in the privacy tools themselves; these flaws can leak data without a hacker doing anything. This leakage happens when an error or design flaw makes a VPN share user information that should be private. There are different causes for this data leakage, but knowing the warning signs and understanding how to address the problem if you encounter it is key.
For example, IP address leakage is when a VPN accidentally shares a user’s real IP address. This can have dangerous consequences, especially for people who are in touchy political situations. However, IP leaks are easy to spot. If you use a VPN to go on a site or service that normally would be blocked where you live, and it still says it’s blocked when the VPN is turned on, there might be an IP leak.
Malicious Extensions or Applications
In some cases, hackers can gain access to a user’s data through malicious extensions or applications. It’s important to only download reputable VPNs and avoid free or unknown options that may not have the necessary security measures in place.
Additionally, always be cautious when sharing personal information online, as hackers can use this information to access your accounts and potentially your VPN. Keep all of your software and programs up-to-date to prevent any vulnerabilities that hackers may exploit.
While it is possible for a VPN to be hacked, taking steps toward strengthening your online security can make it much harder for attackers to access your data. Always prioritize using strong passwords, reliable encryption standards, and being cautious about what you download onto your devices. Doing so can significantly reduce the likelihood of your VPN being hacked.
Unsecured Wi-Fi Networks
Another way that hackers can potentially access your data through a VPN is by using unsecured Wi-Fi networks. Connecting to public Wi-Fi without a VPN leaves you vulnerable to attacks, and even if you are using a VPN, it’s important to make sure the network itself is secure as well. Only connect to trusted and encrypted networks when using a VPN for added protection.
Untrustworthy VPN Providers
Unfortunately, not all VPN providers can be trusted to keep your data secure. Some may log in and sell user information, or even actively cooperate with hackers themselves.
Overall, while there may be weaknesses in some VPNs, taking steps toward improving your online security can greatly reduce the chances of being hacked. Remember to always prioritize strong passwords and encryption standards, watch out for malicious extensions or applications, and only connect to secure networks. By keeping these precautions in mind, you can effectively protect yourself from potential VPN hacking.
Lack of Awareness and Education
Many users may not be aware of proper security measures or the potential vulnerabilities of their VPN. Educating yourself on online privacy and taking steps to protect your information can go a long way toward preventing hacking attempts on your VPN. Additionally, using reputable and trustworthy VPN providers can also help ensure that your data is properly protected [3].
In conclusion, while it is possible for a VPN to be hacked, there are steps that can be taken to prevent this from happening. Stay cautious and informed about online security practices, and prioritize using reliable VPNs and encryption methods. By being proactive about protecting your information, you can effectively reduce the chances of your VPN being hacked.
How Can a VPN Service Be Hacked
Through Vulnerabilities In VPN Protocols
The most common protocols used in consumer VPN services include OpenVPN, WireGuard, and IPsec. These protocols describe the rules that your VPN uses to create a secure connection between your device and the VPN server.
Depending on the VPN service you use, you may or may not be able to choose your preferred protocol. Keep in mind that each protocol possesses its own advantages and disadvantages, with some being much more secure than others.
Some VPN protocols are more secure than others.
If there is even a tiny security flaw in the protocol you’re using, your whole VPN connection could be hacked. This might occur because of design flaws if the protocol is still new, or simply because the VPN client wasn’t installed correctly.
For instance, due to reports that the NSA cracked a PPTP VPN connection to spy on a target, the PPTP protocol is no longer considered secure. Despite being outdated, it is still included as an option by some VPN services.
Through Cryptographic Attacks
A VPN will convert your web traffic into an unintelligible code by using what is called an encryption cipher. This algorithm is used to encrypt and decrypt data. In order for extra security, hash authentication is also implemented along with the cipher.
The three most utilized ciphers among VPN providers are AES, ChaCha20, and Blowfish.
The number of digits in the encryption key is called a key length. In general, longer keys are stronger and more secure. For example, AES-256 is better than AES-128.
A good VPN will use the AES-128 cipher to encrypt your data.
As computing technology advances, so too does the risk of hacking. Because older hash functions and encryption ciphers can be broken more easily, it’s possible for a hacker to break into a VPN connection that uses an outdated cipher.
For instance, the SHA-1 hash function is no longer secure, and Blowfish cipher can be beaten using “birthday attacks”. These cryptographic functions are still used by some lower-quality VPNs.
Anything less than AES-128 is not recommended for a VPN to encrypt your data. However, if using WireGuard, ChaCha20 is a secure alternative that uses 256 bits and therefore, is just as safe as AES-256 encryption [4].
Through IP, DNS, or WebRTC leaks
One of the main advantages of using a VPN is that it hides your IP address, allowing for true online anonymity and protection from tracking. However, if there is a DNS leak or WebRTC leak, your actual IP could be revealed.
This can happen if you have not correctly set up the VPN on your device or if the VPN service has poor security measures in place. It’s important to use a reputable VPN provider and make sure to test for leaks before trusting your privacy to the VPN connection.
Furthermore, some internet providers will attempt to block VPN traffic through deep packet inspection (DPI). This can result in your real IP being exposed even when using a VPN. To prevent this, select a reputable service that offers obfuscation technology, such as NordVPN’s “Obfuscated Servers” or ExpressVPN’s “Stealth Mode”.

In short, a VPN can be hacked through vulnerabilities in its protocols, cryptographic attacks on its encryption, and IP/DNS/WebRTC leaks. However, by choosing a reputable provider with strong security measures and staying vigilant about testing for leaks, the risk of hacking can be greatly minimized.
By Compromising a VPN Server
Another vulnerability to consider is the potential for a hacker to compromise a VPN server. This can occur through various means, such as getting access to the server’s administrative credentials or exploiting vulnerabilities in the server’s software.
If successful, this type of attack would allow the hacker to monitor and potentially modify any data passing through that server. However, it should be noted that reputable VPN providers have strict security protocols in place, including secure servers and frequent monitoring for any potential breaches.
In addition, some VPN services offer additional measures such as multi-hop connectivity and “kill switches” to ensure your data stays safe even if there is a breach on one of their servers. It is important to choose a provider that takes these extra precautions.
By Stealing Encryption Keys
If hackers manage to get ahold of the encryption keys used to secure your data, they could easily hack into your VPN connection and read all traffic – both incoming and outgoing.

Most top-tier VPNs use Perfect Forward Secrecy (PFS) by default, which fortunately encapsulates its encryption keys.
The PFS, or Perfect Forward Secrecy protocol feature, guarantees that your VPN server and the client will use different keys for every new VPN session. This makes it impossible for curious third parties to decrypt past traffic even if they’ve somehow managed to acquire the key used in a previous session.
Essentially, Perfect Forward Secrecy prevents a single encryption key from compromising all your VPN sessions if it were to be discovered. The temporary keys make certain that a hacker could only access one particular session at any given time, and nothing beyond that.
Tips for users: if your VPN is based in a country that is part of the Five Eyes, government agencies may be able to access your identity and activity. Some countries have the legal right to force VPN companies to log in and share your data [5].
Bypassing Authentication
Finally, a hacker may also try to bypass authentication measures in order to gain access to your VPN connection. This can be achieved through various means, such as phishing attempts or malware that steals login credentials.
To prevent this type of attack, make sure to use strong and unique passwords for all your accounts and never enter sensitive information on insecure websites. It’s also important to have solid anti-virus software and practice safe browsing habits. Additionally, some VPN providers offer multi-factor authentication for added security.
Cracking Encryption
Another potential vulnerability involves a hacker attempting to crack the encryption used by the VPN. This is a complicated and time-intensive process, but it is technically possible if the encryption protocol has weaknesses or if a brute force attack is used.
To prevent this type of attack, select a reputable VPN provider that uses strong encryption protocols such as AES-256, and regularly updates its software to patch any vulnerabilities.
While there is always a potential for hacking, taking these preventive measures can greatly reduce the risk and ensure that your data stays safe through a VPN connection.
Man-in-The-Middle Attacks
A Man-in-the-Middle attack is enacted when the attacker essentially lies between two devices communicating with each other and reading or changing the traffic being exchanged. This type of cryptographic attack can often go undetected, as the attacker could pretend to be one of the devices in question [6].
DNS Hijacking
DNS hijacking is a serious cyber-attack where an attacker can redirect your DNS traffic to a malicious server. This allows them to intercept your internet traffic and possibly steal private data if you’re not using a secure connection. Protect yourself by being aware of the dangers of DNS hijacking and taking steps to prevent it.
IP Address Spoofing
In IP address spoofing, a hacker alters the source IP address in their communications with your device, disguising their identity and making it harder to trace the attack back to them. This method can also be used to access restricted networks or send harmful content under a false identity. To protect against IP spoofing, use strong network security measures and monitor for unusual activity.
ARP Cache Poisoning
ARP cache poisoning is dangerous because it gives hackers the ability to access private information sent over the network.
There are 2 ways this vulnerability can be exploited by hackers:
- To conduct a man-in-the-middle attack, hackers create a fake ARP message that tricks computers on the network into thinking that the hacker’s computer is actually the router. This allows them to intercept and redirect all traffic meant for the router, giving them access to sensitive data;
- The hacker creates a false ARP message that tricks the other computers on the network into thinking the hacker’s computer has a different IP address. This diversion of traffic allows the hacker to access information or files they otherwise would not be able to;
Session Hijacking
Session hijacking, also known as “sidejacking,” is a type of attack where hackers steal cookies from your internet browser that contain session information. This allows them to access your online accounts or applications without needing credentials, posing a serious threat to sensitive data and privacy. Protect yourself by using strong passwords, avoiding public networks, and regularly clearing your browser’s cookies [7].
Malware
Malware is software created to harm or disable a computer system. There are many ways it can be contracted, such as through email attachments, downloads from malicious websites, and USB devices with malware embedded in them.
The malware allows attackers to not only access the device it’s present on, but also any networks associated with that device – even a VPN.
Phishing
Another way to hack VPNs is through phishing scams.
The malicious link puts the user on a false website that looks like the login page for their VPN. By obtaining their login information, the attacker can then access the VPN themselves.
The hacker could also send an email that looks like it’s from the VPN provider, but instead, the link leads to a fake and harmful website.
What Happens If Your VPN Is Hacked
Surveillance
If your VPN connection is hacked and security keys are leaked or encryption ciphers are weak, then anyone including the government, your ISP, or a malicious third party could see your browsing activity. If this happens, the spying third party would need to have access to the leaked keys or be able to break the encryption cipher [8].

Furthermore, if a hacker gets access to the VPN server you’re logged into and it’s configured to keep activity logs, they could be capable of monitoring your past, present, and future actions on that one server.
Sensitive data leaks
If your VPN is hacked, any sensitive information you transmit online – like passwords, credit card numbers, or bank account details – could potentially be stolen by the attacker. They could also install malware on your device to further compromise your security and privacy.
Vulnerability to MitM Attacks & Malware
While hacking a VPN does not immediately infect your device with malware, it can allow hackers to more easily access and infect your device with other malicious software.
Without a safe and secure VPN, you’re just as susceptible to attacks on public WiFi networks.
Attackers can tamper with crucial parts of network traffic, reroute this traffic, or inject harmful content into an existing data packet on an unsecured network. If a hacker gets access to your DNS requests and sends you to a DNS server that they’re in control of, this is called a Man-in-the-Middle (MitM) attack [9].
If you’re unsuspecting, it’s easy for someone who has hacked your device to show you counterfeit websites or login forms that appear real. These fake sites can be used to obtain your passwords by tricking you into entering them.
What To Do If Your VPN Has Been Hacked?
If you have used a low-quality VPN that has experienced data leakage or if you fear your VPN connection has been hacked, then we suggest the following measures:
- Immediately stop using the VPN to prevent additional damage;
- Uninstall the VPN from every device you own, and then turn each one back on;
- Completely remove VPN extensions from all browsers and routers, including any residual files, then restart the devices;
- Please change any personal information that may have been impacted by this (i.e. usernames, passwords, SSH keys);
How to Choose a Secure VPN That’s Near Impossible to Hack
Select a VPN With AES 256-bit Encryption
If you’re looking for a VPN that will keep your information private, check to see if it has AES 256-bit Encryption. This is the strongest form of encryption available, and it creates long and complex keys that instantly deter hackers. Most experts use ExpressVPN, which has never been hacked and is endorsed by the US government to protect sensitive information [10].
Find a VPN With OpenVPN/IKEv2 Protocols
While there are a number of VPN protocols available, OpenVPN and IKEv2 reign among the best. OpenVPN is especially popular because it is an open-source protocol that is regularly updated and maintained. On the other hand, IKEv2 boasts speed and stability while being compatible with more platforms than OpenVPN – though the latter requires the installation of third-party software.
Choose a VPN With SHA-2 Authentication
SHA-2 is the latest and most secure authentication available today. It allows you to receive information free of trackers and malware. Many VPNs utilize SHA-2 authentication to keep you safe when sending and receiving data. SHA authentication has a history of being hacked. For example, SHA-1 was hacked numerous times in the past. Experts recommend avoiding these variations of SHA authentication.
Check the VPNs Server Network Management Policies
To ensure you are defended against cyberattacks, you must check and understand a VPN server’s network management policies before committing. For example, if the VPN doesn’t have control over its network, be sure that it has military-grade encryption to protect any third-party servers.
Interestingly, VPN providers have shifted from regular hard-drive servers to more secure RAM servers that protect your data from hackers and don’t require as much maintenance. RAM servers allow the VPN to erase all collected data after every reboot, leaving no data at risk of being stolen by hackers. If you’re looking for the safest and most secure VPN, be sure that they own their network of RAM servers.
Test the VPNs IP Address and DNS Leak Protection
IP and DNS leaks present huge security risks by giving hackers access to your IP address, location, and identity. Leak protection prevents this from happening, keeping you safe from prying eyes.
Most experts were motivated to get a VPN with leak protection after finding out how easy it is for hackers to steal my information. This should be one of your top priorities when considering online safety.
If you want to see for yourself whether an IP address or DNS leak can occur, use the IP address tool and DNS leak test.
Investigate and Select a VPN With a No-Logs Policy
A no-logs policy means that the VPN provider doesn’t have any record of your online activity, giving you added privacy and security. It’s important to note that while a VPN may have a no-logs policy, it may still log data related to technical reasons or for maintenance. Always do your research before committing to a VPN to ensure they have a strict no-logs policy and do not log any data.
Check for Advanced Features That Block Malware and Ads
By using a VPN with ad and malware blockers, you can avoid having third-party trackers installed on your device through advertisements or malicious links. These trackers typically install malicious software onto your device that collects your personal data without you knowing. Furthermore, devices infected with viruses often run slowly until the owner gets premium anti-virus software or does a factory reset [11].
What Does A VPN Actually Protect You From
If A Third-Party Website Is Breached
If hackers infiltrate the database of a website you frequently visit, they could potentially read any unencrypted data stored on that server. This would include sensitive personal information like your email address, password, and contact info. While using a VPN can mask your IP address and provide some measure of protection, it will not hide other identifying information you may have submitted.
If Your Device Is Already Infected
If your device is already under the control of hackers, they can use elevated privileges to record what’s on your screen, document your keystrokes, and turn on your camera and microphone. In this scenario, opting into a VPN will not restrict the hacker’s access to your computer.
If You Download and Install Malicious Software
If you install software from an untrustworthy source, a VPN cannot protect you. Downloading unknown software can also result in malware being installed on your device without you realizing it. Additionally, some browser extensions can put your privacy and security at risk.
Though a VPN will encrypt your internet connection, it can’t protect you if you use malicious USB drives, hubs, or cables that are infected with malware.
If You Click a Malicious Link
VPNs will not save you from phishing scams or other social engineering ploys. Be responsible for the links you click and the files you download to your device.
Although some VPNs have features that can protect against DNS requests to known malicious URLs, thus reducing the likelihood of a phishing attack, these tools are not foolproof.
If Another Device In Your Local Network Is Infected
If there is another infected device on the same local network as your computer, hackers could theoretically use a technique called ARP spoofing to infect your machine as well.
The level of protection a VPN can provide in this situation varies depending on how the network is configured.
FAQ
Are premium VPNs really secure?
While it is true that a premium VPN service may have better security measures in place compared to a free or low-cost option, no VPN can claim to be completely secure. Additionally, the level of security offered by any given VPN also depends on the provider’s capabilities and commitment to keeping their network safe.
Can my personal information or data be accessed while using a VPN?
It is possible for your personal information and data to be accessed while using a VPN, especially if the hacker is targeting you specifically. However, a properly configured and securely run VPN should provide an extra layer of protection against such attacks. It’s important to do your research and choose a reputable VPN provider, as well as take steps to protect yourself online (such as using strong passwords and enabling two-factor authentication).
What does a VPN not protect you from?
While a VPN gives you someplace to hide, it’s not enough by itself. You’re still vulnerable to online dangers like malware and ransomware if you don’t have antivirus software too. A VPN also doesn’t protect you from things like phishing scams or fraudulent websites. And, as mentioned before, if a hacker is specifically targeting you, it may be possible for them to bypass the protection offered by a VPN [12].
Should you keep the VPN on all the time?
It’s generally recommended to use a VPN whenever you’re connected to the internet, especially when accessing sensitive information or performing online transactions. However, some VPNs can slow down your internet connection and there may be times when it’s not necessary (such as when using a trusted network at home). It ultimately depends on your own level of risk tolerance and personal preferences. With that said, it’s always better to err on the side of caution and keep the VPN turned on.
Can the police track a VPN?
Even though police can’t track live, encrypted VPN traffic, if they have a court order and go to your ISP (Internet Service Provider), these providers can give law enforcement officials access to connection or usage logs that show that you’re using a VPN [13].
Can a VPN steal your passwords?
In theory, a malicious VPN provider could potentially steal your passwords or spy on your online activity if they wanted to. This is why it’s important to do thorough research and choose a reputable, trustworthy VPN provider. A good VPN will have strong encryption measures in place to protect your data and clear policies about logging user information. In addition, you can use additional security measures such as using a password manager and two-factor authentication for extra protection.
Can someone see my internet history if I use their WiFi with VPN?
By establishing a secure connection, VPNs make it impossible for outsiders to see what activities you’re doing online. So, if you’re using a WiFi router or an Internet service provider, all they would be able to observe is encrypted data [14].
How do you tell if an IP address is a VPN?
You can use websites, CLI, or scripts to identify if an IP address is a VPN by examining its hostname.
If the hostname corresponds with a VPN provider, this will confirm that the IP address is indeed associated with a virtual private network [15].
Do I really need a VPN at home?
While a VPN can offer added security and privacy when browsing the internet, it is not foolproof. A hacker can potentially gain access to your personal information or data if they are able to break through the VPN’s encryption.
It is important to note that using a reputable and trusted VPN service can greatly reduce the chances of being hacked. Additionally, taking precautions such as using strong passwords and avoiding suspicious websites can also help protect against hacking attempts.
Ultimately, whether or not you choose to use a VPN at home depends on your own level of concern for privacy and security. However, for those who handle sensitive information or frequently use public Wi-Fi networks, a VPN may be worth considering.
Is banking safe with a VPN?
While a VPN can add an extra layer of security to your online banking activities, it is important to note that no technology is completely foolproof. As with any system connected to the internet, a VPN can potentially be hacked. However, reputable VPN providers continuously update their encryption protocols and security measures to protect against potential attacks.
It is also important for users to take responsibility for their own online safety by choosing strong passwords, keeping their software and operating systems up-to-date, and avoiding suspicious websites or links. Additionally, using multi-factor authentication can provide added protection for sensitive financial transactions.
Does private browsing protect you from hackers?
The short answer is no, a virtual private network (VPN) can still be hacked. While a VPN does provide an extra layer of security and privacy, it is not a foolproof solution.
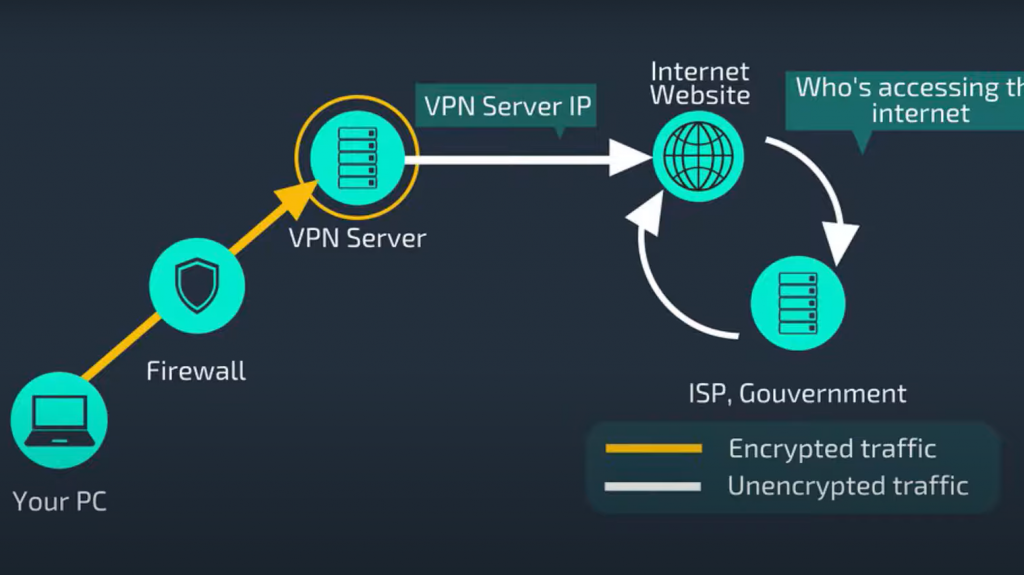
There are several ways that a hacker could potentially access and decrypt your data while using a VPN:
- One common method is through vulnerable software on the user’s device or network;
- Another potential vulnerability is when using a shared or public VPN server, as the traffic could potentially be intercepted by another user on the same server;
It’s important to remember that a VPN can only protect the information being sent through its encrypted tunnel. If a hacker gains access to your device or account credentials outside of the VPN, they can still potentially access your data.
To best protect yourself from hackers, it’s important to regularly update all software on your devices and use strong, unique passwords for all accounts. Additionally, doing research on the VPN provider before choosing one and only using reputable providers can also help to reduce the risk of a hack.
Useful Video: Can A VPN Be Hacked? (Easy Guide to Find Safe VPNs in 2023)
References:
- https://blog.orchid.com/what-happens-when-a-vpn-gets-hacked/
- https://www.vpnmentor.com/blog/can-vpns-hacked-take-deeper-look/
- https://www.cyberghostvpn.com/en_US/privacyhub/can-a-vpn-be-hacked/
- https://www.top10vpn.com/guides/can-a-vpn-be-hacked/
- https://vpnalert.com/resources/can-vpn-be-hacked/
- https://en.wikipedia.org/wiki/Man-in-the-middle_attack
- https://en.wikipedia.org/wiki/Session_hijacking
- https://www.top10vpn.com/guides/can-a-vpn-be-hacked/
- https://www.top10vpn.com/guides/can-a-vpn-be-hacked/
- https://www.wizcase.com/blog/how-secure-is-your-vpn-and-how-to-protect-yourself/
- https://www.wizcase.com/blog/how-secure-is-your-vpn-and-how-to-protect-yourself/
- https://www.cyberghostvpn.com/en_US/privacyhub/what-does-vpn-hide
- https://surfshark.com/blog/can-police-track-vpn
- https://www.broadlinc.com/news/can-a-wifi-owner-see-what-sites-i-visited-in-incognito-mode
- https://www.abstractapi.com/guides/how-to-detect-if-an-ip-address-is-using-a-vpn








Leave a Reply